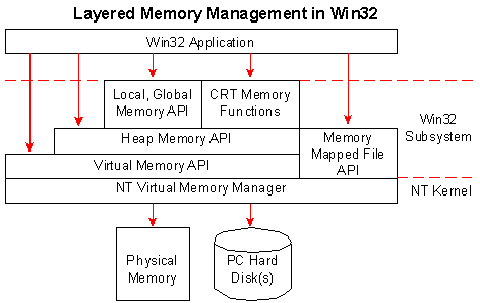
GuidedHacking on X: "🕵️Detecting Sus Threads with Memory Checks 💡 Strategies for Evading Thread Detection ➡️https://t.co/3yK8DKczlr https://t.co/PA7ooVvPPE" / X
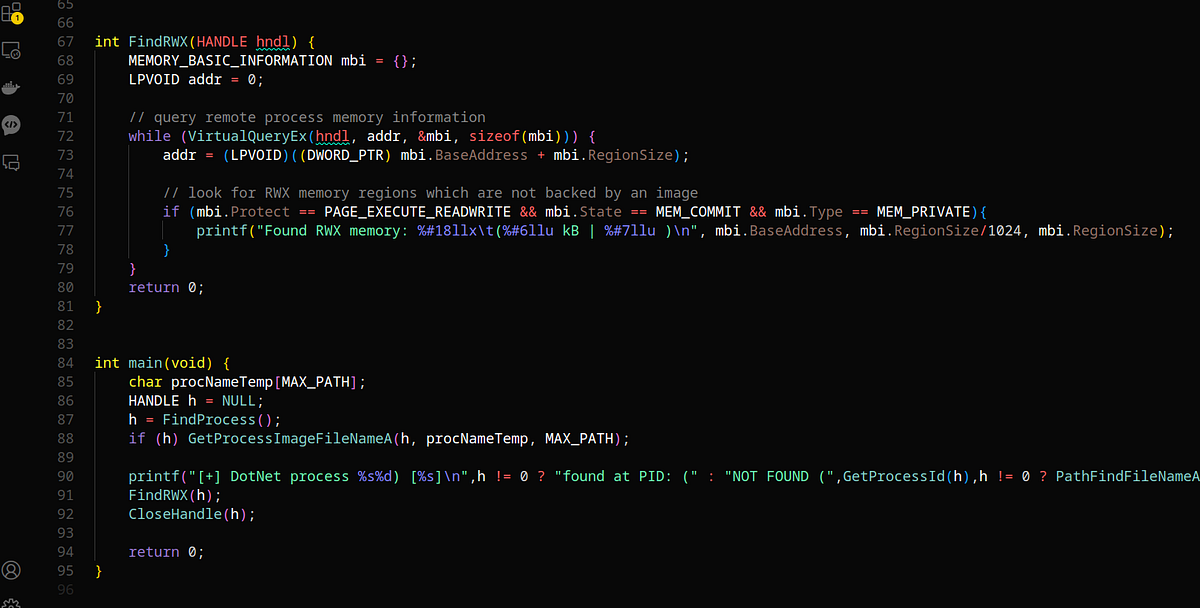
Find RWX Memory Spaces. Hey there, tech enthusiasts and fellow… | by S12 - H4CK | Oct, 2023 | Medium