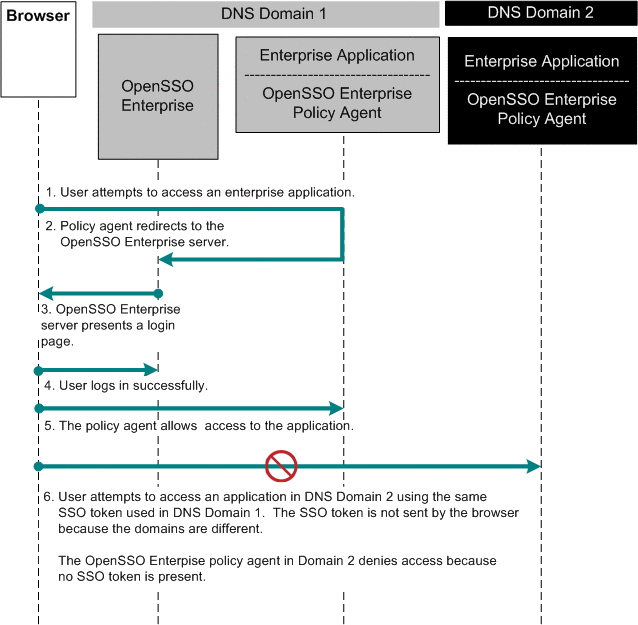
Chapter 16 Implementing Cross-Domain Single Sign-On with Cookie Hijacking Prevention (Sun OpenSSO Enterprise 8.0 Deployment Planning Guide)

Figure 1 from Cross-Domain Grid Authentication and Authorization Scheme Based on Trust Management and Delegation | Semantic Scholar
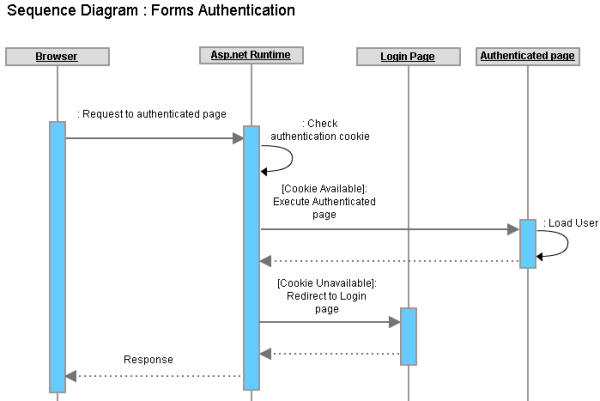
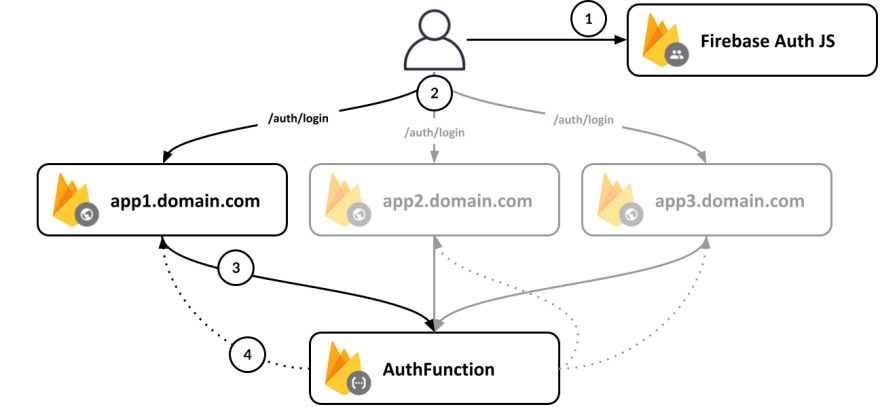
Single Sign On (SSO) for cross-domain ASP.NET applications: Part-I - The design blue print - CodeProject

Cross-domain Authentication Mechanism Design and Research Based on the Mobile Internet | Semantic Scholar
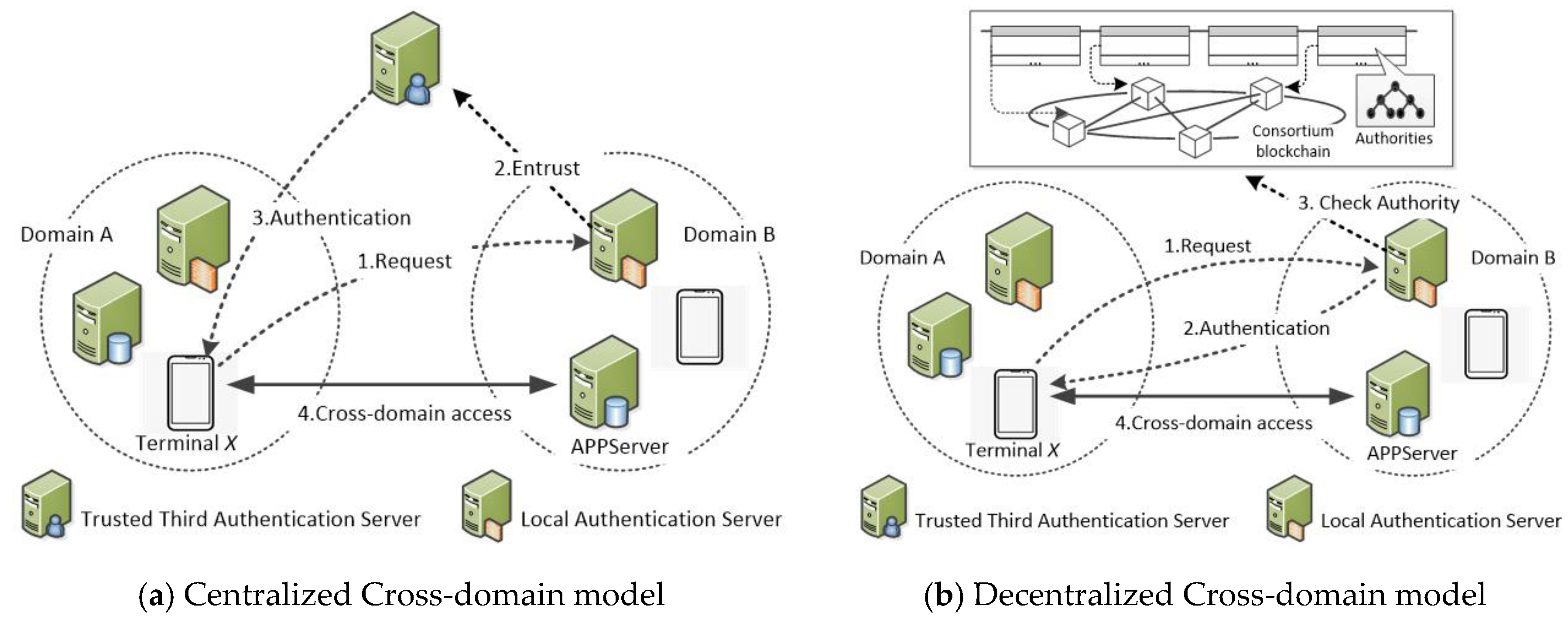
Electronics | Free Full-Text | IRBA: An Identity-Based Cross-Domain Authentication Scheme for the Internet of Things

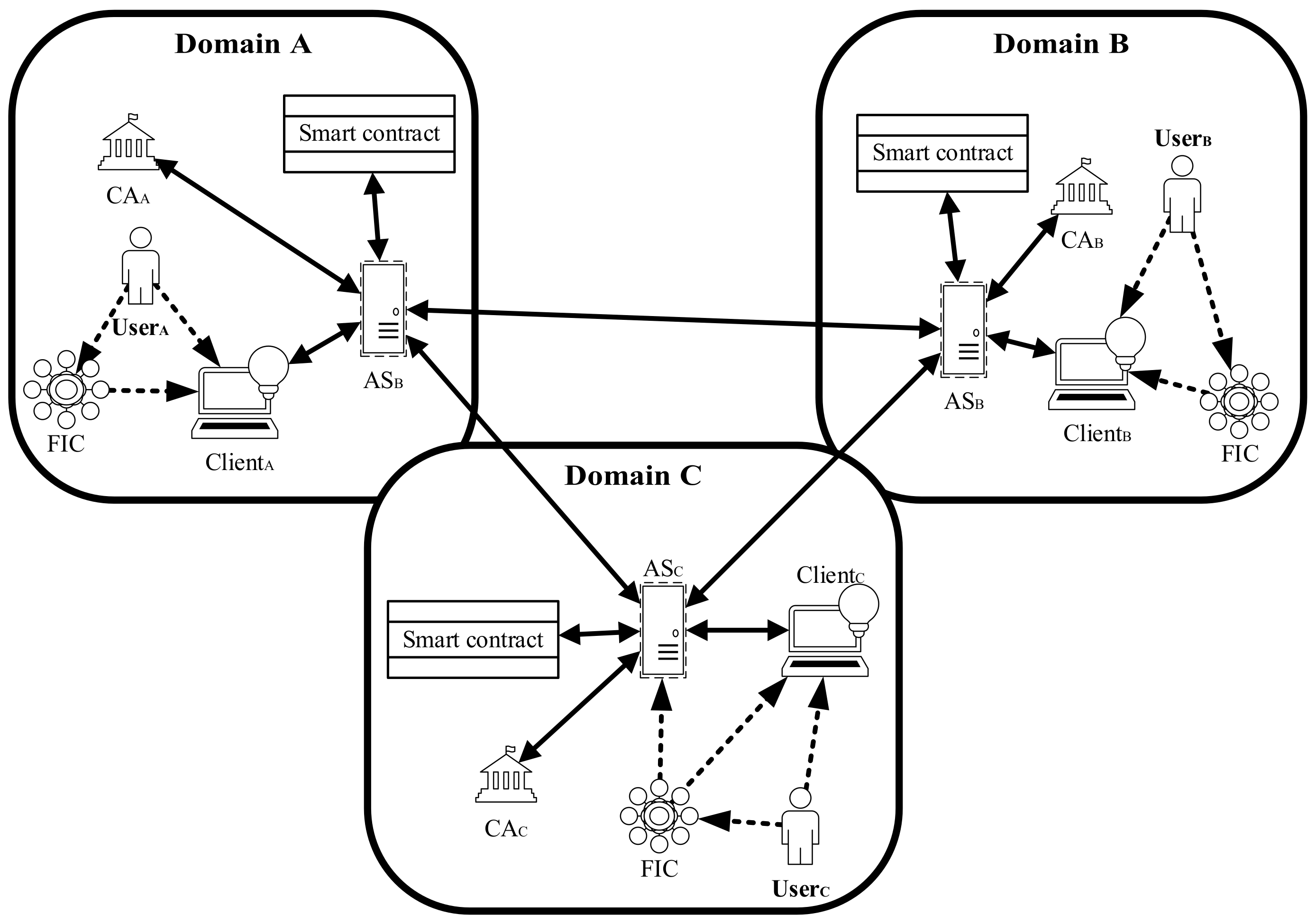
Cross-domain authentication and authorization of users and services.... | Download Scientific Diagram
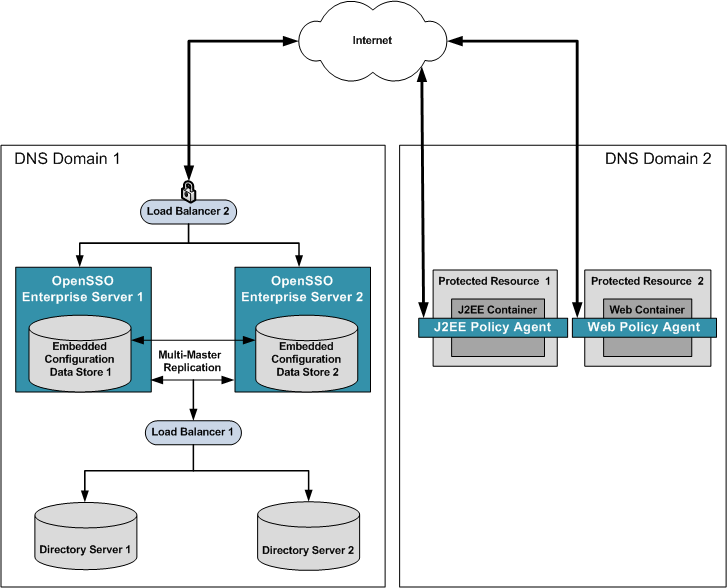
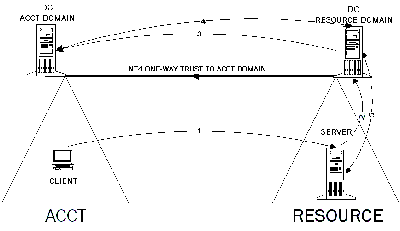
Chapter 16 Implementing Cross-Domain Single Sign-On with Cookie Hijacking Prevention (Sun OpenSSO Enterprise 8.0 Deployment Planning Guide)
![PDF] Blockchain-Assisted Secure Device Authentication for Cross-Domain Industrial IoT | Semantic Scholar PDF] Blockchain-Assisted Secure Device Authentication for Cross-Domain Industrial IoT | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/420e4c9025b0397a812b4579b925d300108568a2/5-Figure2-1.png)
PDF] Blockchain-Assisted Secure Device Authentication for Cross-Domain Industrial IoT | Semantic Scholar

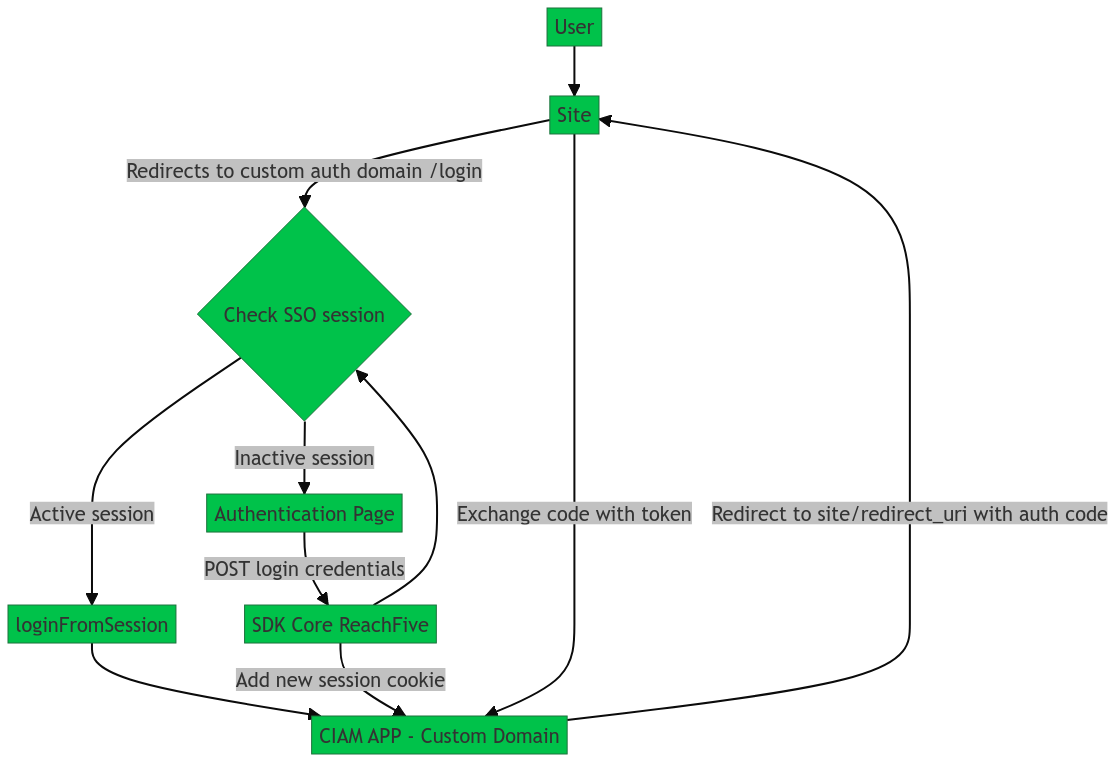
Alex Xu on X: "8/10 🔹By using SSO (single sign-on), you can sign on only once and log in to multiple websites. It uses CAS (central authentication service) to maintain cross-site information

Heterogeneous Cross-Domain Identity Authentication Scheme Based on Proxy Resignature in Cloud Environment